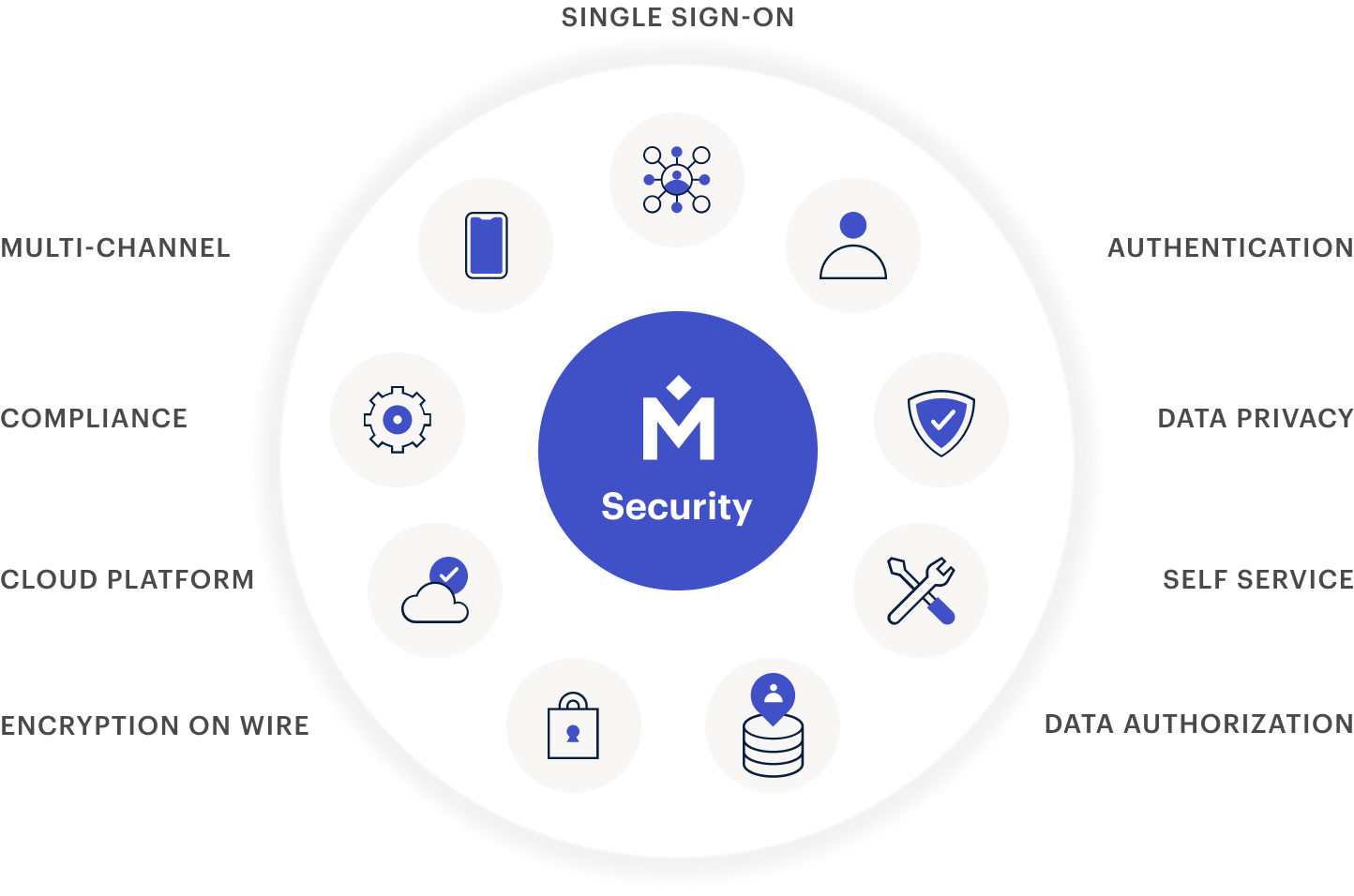
Learn how the Medallia Experience Cloud controls data access and security, and ensures compliance with information security regulatory requirements.
You can be rest assured knowing that the confidentiality, integrity, and availability of your data is protected according to rigorous industry standards. We possess SOC 2 Type II platform compliance, GDPR/SCCs, CCPA, and HIPAA in addition to HITRUST, ISO 27001, 27017, 27018, and 27701. We are also certified for CBPR and PRP.
Medallia maintains up-to-date processes and controls with regular audits by internal and external parties, including clients and independent assessors.